In recent weeks, terms like OIDC and OAuth, Keycloak and Azure were frequently mentioned in our internal discussions. Not everybody is familiar with these terms, and so we will explain them in a way that non-developers can understand what it is all about. Sooner or later, everybody will get in touch with these concepts, which will bring some changes but in the end all users will benefit from their security and convenience every day.
Our experienced DEV-Ops specialist sums up the benefits as follows:
“OIDC enables simple, trustworthy and secure logins which reduce passwords and meximize convenience.”
Login with Microsoft or Google
Many users are already familiar with the principle: A lot of applications allow logging in with existing accounts like Google or Microsoft or other specialized services as shown in the screenshot from Katalon, a tool we use for automatted testing.
A new user does not have to create and remember new login data for a new application and can start right away.
It sounds easy and makes the login process smoother. However, it is up to each individual to decide whether he or she wants to use services like Google or Microsoft as these providers may potentially use the data to create user profiles.
But the concepts for professional use go much further than this, offer additional functions and do not use private Google accounts.
The basics
OIDC stands for OpenID Connect, an authentication protocol built on top of OAuth. OAuth stands for Open Authorization, a framework enabling authorization processes. It is important to understand the meaning of these two central terms, authentication and authorization, and not to mess them up:
Authentication
This steps checks whether the person is really the one he or she pretends to be.
Imagine a bouncer at a club door: He checks your ID card to verify whether you are the legal holder of this ID card and whether you are allowed to enter the building. Once authenticated, you get access to the lobby.
In Cartago Designer you get to the start page after successful authentication.
Authorization
This step checks what you are allowed to do and which areas your are allowed to access.
In our practical example you are standing in the lobby in front of many locked doors. Your access rights determine now which room(s) you can enter, based on your user role.
In Cartago Designer a user has individual user rights, allowing him to open defined folders, to edit or save templates, to just read some template, not to see some of them at all or to do other special tasks.
The users and their roles have to be entered in the OIDC-system by the administrator. As this is not possible for logins with Microsoft or Google, they can only be used for applications without roles, i.e. only for authorization.
IAM
These three letters stand for Identity and Acess Management and include authentification and authorization.
Usually login data is stored locally in files or databases of the application. Modern IAM-systems combine centralized management with high security standards. You can either use an individual server and the Open Source Tool Keycloak or a commercial system such as Entra ID by Microsoft or the services by Google or other players.
Token
Tokens are a core component of OAuth and OIDC. They are used to exchange informations between the applications. There are ID- and access tokens. They contain user information and access rights, have limited validity and are encrypted to prevent tampering. They can also be renewed as needed.
The process
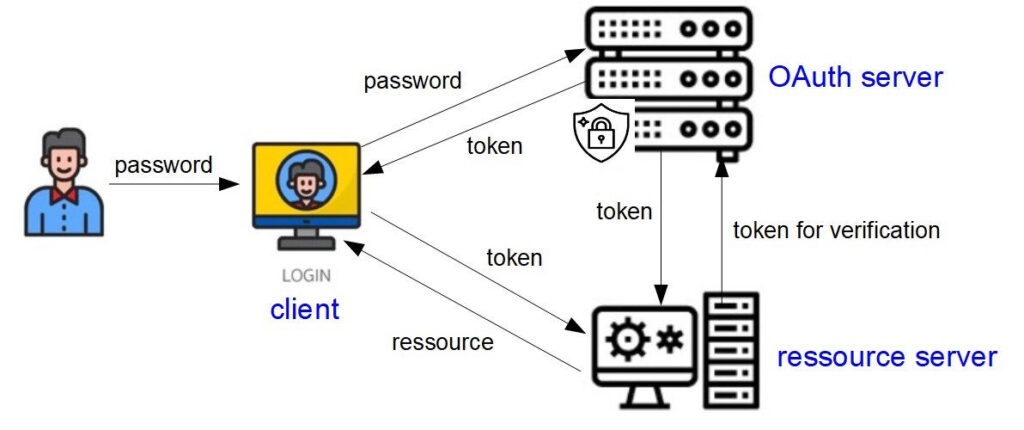
The user calls the application in his client. The latter communicates with the OAuth server and requests the access token for the given password. As soon as the client got this token he sends it to the ressource server, which gives access to the ressource.
The ressource server can also communicate directly with the OAuth server to request the check of a token or the reneval of an expired token.
System requirements
Such a comprehensive solutions requires appropriate systems. If user management is done centrally for all systems of a company, the solution must be fail-save. One server is not enough. A sophisticated backup-system may be composed of up to 6 servers.
Benefits of OAuth and OIDC
Einhanced security
Credentials are no longer stored in the application and thus for n application in n places, but centrally. This central storage, the OIDC provider, is a specialist for this task and offers high security standards with multi-factor authentication.
Access is done in several steps preventing abuse. Most of the time the user has a password, but there will often be additional elements such as a token sent to a smartphone, a finger print or facial recognition.
The time of standard passwords which can easily be remembered but also stolen will end sooner or later.
Single Sign On
If you login with your central data to the OIDC provider in the morning, e.g. your Microsoft account, you will automatically get access to other applications using this provider. You do not need to login to Cartago Designer or Workspace separately.
Simplified User-Management
Before a new member of staff can start work, the roles have to be set up in the OIDC-system for every application. If a member of staff leaves the company, only the user has to be disabled in the OIDC system. After this he can no longer access the corresponding applications. This is much easier and more reliable than disabling access to every single system.
Standardization
The greatest actors are companies such as Microsoft, Amazon or Google. They are member of the OpenID-foundation, establishing standards going beyond platforms and systems.
Implementation
Our past implementations of OIDC and OAuth for different customers had some steps in common and some differences depending on the provider and the individual concepts for rights and roles. Our work showed us that introducing OAuth and OIDC is a significant step toward greater security and user convenience.
„It is an investment in the future – both for our clients and ourselves“,
says our CEO Manuel Niemeyer.
If you are interested in an integration of this additional functionality for security and comfort, please contact us for further information.